The Architecture of PAM360
Now that you have finished learning the basic concepts of PAM360, you may now proceed to get to know how exactly PAM360 works, its overall architecture, and the process flow. This document provides a comprehensive architectural overview of the PAM360 system by focusing on different key quality attributes.
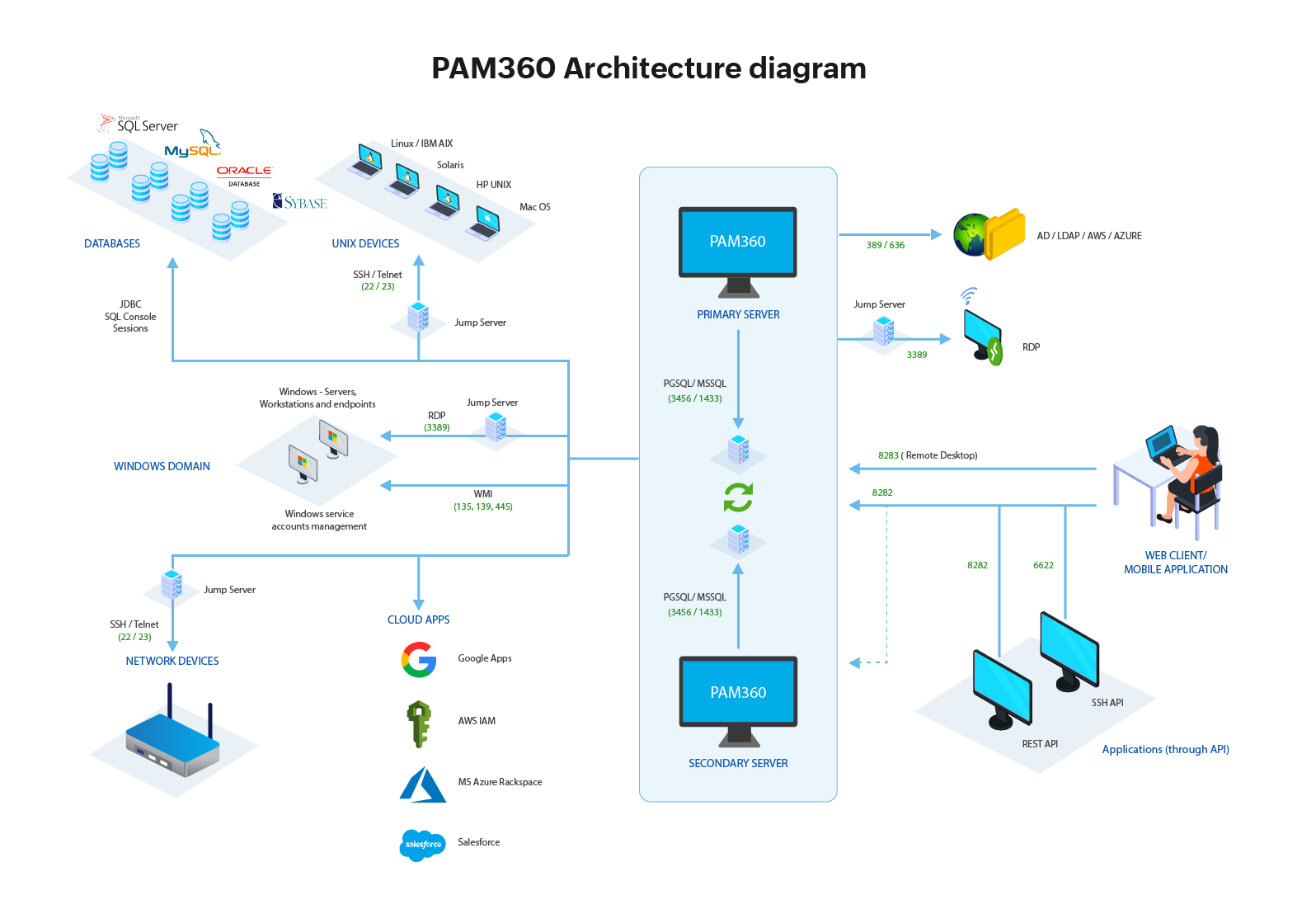
The below diagram thoroughly illustrates the complete functional architecture of PAM360.
The above illustrations depict the different components of PAM360 and how they interact with each other. Read further to know more about each component and their functionalities in detail.
1. Different Components in PAM360
PAM360 comprises of multiple components that work in hand with each other to protect your enterprise passwords and strengthen security in your environment. Read further to know more about each component in details. To know more about the list of modules and features in PAM360, click here.
PAM360 can be installed in any Windows and Unix based machines as a web application. These systems can be configured based on the users' requirements. PAM360 is accessible via both Web Clients and Mobile Applications.
PAM360 offers three disaster recovery options to web servers:
A user is an individual who has a user account that has access to the application through a computer or mobile using a network service. Users are identified to the system by the user's id or user's name.
In PAM360, you will be able to import users using Active Directory, Microsoft Entra ID, and LDAP. You can also add users manually, API users or import users using a file. The added users can be assigned with appropriate access roles and password policies. You can also add new user roles with different set of permissions tailored to your needs.
1.3 Supported Databases
PAM360 supports PostgreSQL, MS SQL, Amazon RDS MS SQL, Amazon RDS PgSQL, and MS Azure SQL. By default, PAM360 comes bundled with PostgreSQL. PAM360 allows you to migrate from one database to another as per your convenience.
1.4 Resource Types
Resources in PAM360 refer to any server, application, network device, or appliance in your environment that has authentication credentials that need to be secured. PAM360 supports various database types, Unix devices, Windows Domains, Cloud apps, and network devices. PAM360 allows you to discover a variety of devices such as Windows, Linux, VMware and Network devices.
1.5 Supported API's
In PAM360, users are allowed to choose between the two API types which are SSH CLI, and RESTful API. Users can configure and use PAM360 API's for application to application password management.
2. Process Flow
Right until now you have read about the different components of PAM360. In this section, you will learn in detail how these components work and interact with each other to provide a seamless experience.
PAM360 is an on-premise, self-hosted solution available as a binary for installation on Windows & Linux, which can be configured accordingly based on the user's requirements.
- After installing PAM360, users can access the PAM360 web application through the port 8282 or using the mobile application. Ports play an essential role in PAM360 for remote access. Click here to know about the different ports used by PAM360.
- Also, refer to this document to know more about the initial stages of setting up PAM360 in your environment.
- Now, use the port 3456 to access Postgre SQL or port 1433 to access MS SQL database.
- After setting up the database, administrators can now import users and resources into PAM360 using AD or LDAP using ports 389 and 636 respectively.
- In PAM360, users are allowed to choose between the two API types which are SSH CLI, and RESTful API. Use the port 5522, to establish a SSH CLI connection.
- PAM360 allows you to establish a secure connection to any windows resources via landing servers.
- After associating the resources to the landing server, PAM360 allows you to launch direct connections to the target systems.
- Likely, for connections, respective ports should be opened.
- PAM360 establishes direct connection (using TELNET, SSH or RDP) to the data center. Use the ports 22 and 23 to connect using TELNET and SSH respectively.
- A native port 3389 must be used to establish a successful RDP connection between PAM360 and your target system.
- When the connection is established PAM360 allows users to transfer files to and from the connected machine using the PAM360 session gateway.
- You can also use PAM360 to replace your VPN systems, as the product offers Gateway-based RDP, SSH, and SQL connection features bundled with session recording.