Adding API User Accounts in PAM360
(This procedure is applicable prior to build 6700)
PAM360 allows you to add API users manually. API user accounts are required to configure password management APIs for Application-to-Application password management. You need to create API user accounts in PAM360 for those who will use the password management APIs, where each API user account should be attached to a single endpoint (typically a server or a desktop from which the API is used, so that the user accounts are uniquely identified - for example, as user@hostname).
Note: User addition can be carried out only by Administrators and Privileged Administrators or by custom roles with similar permissions.
Creating an API User Account in PAM360
- Click the Users tab and click Add User >> Add API User from the drop-down menu.
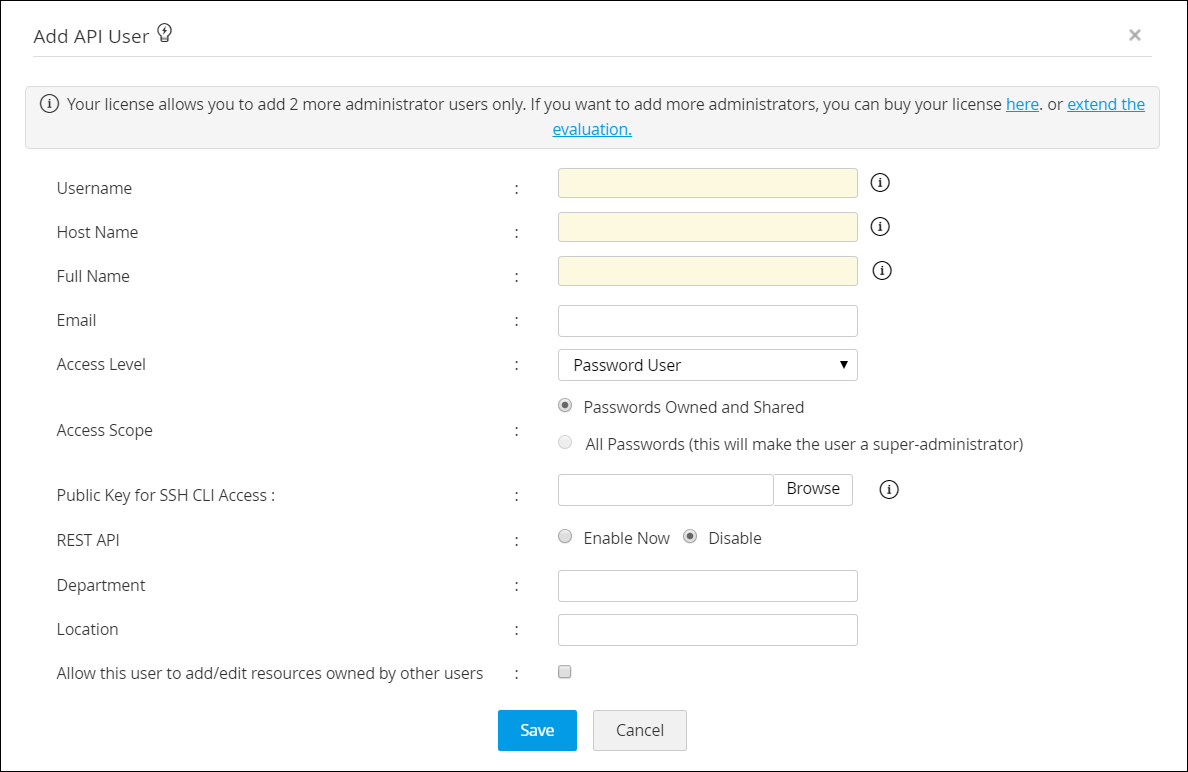
- Enter the Username in the respective text field. This name identifies the API user.
- Enter the name of the host from which the API user would access PAM360 for password management operations.
- Full Name refers to the name with which the API user would be identified in the external world such as reports, audit trails and other places where activities are traced to users.
- Select an Appropriate Access level for the API user being added - Administrator/Password Administrator/Privileged Administrator/Password User/Custom Roles.
- You can use Access Scope to change an Administrator/Password Administrator/Privileged Administrator into a Super Administrator by choosing the option All Passwords in the system. When you do so, they will be able to access all passwords in PAM360 without any restriction. Conversely, a Super Administrator can be changed to their earlier role of Administrator/Password Administrator/Privileged Administrator by choosing the option Passwords Owned and Shared.
- Upload the public key of the user machine from where the user accesses the SSH CLI APIs in the Public Key for SSH CLI Access field. This public key acts as the preliminary layer of the user verification method in addition to the hostname validation.
- Enable REST API by clicking the button Enable Now beside REST API.
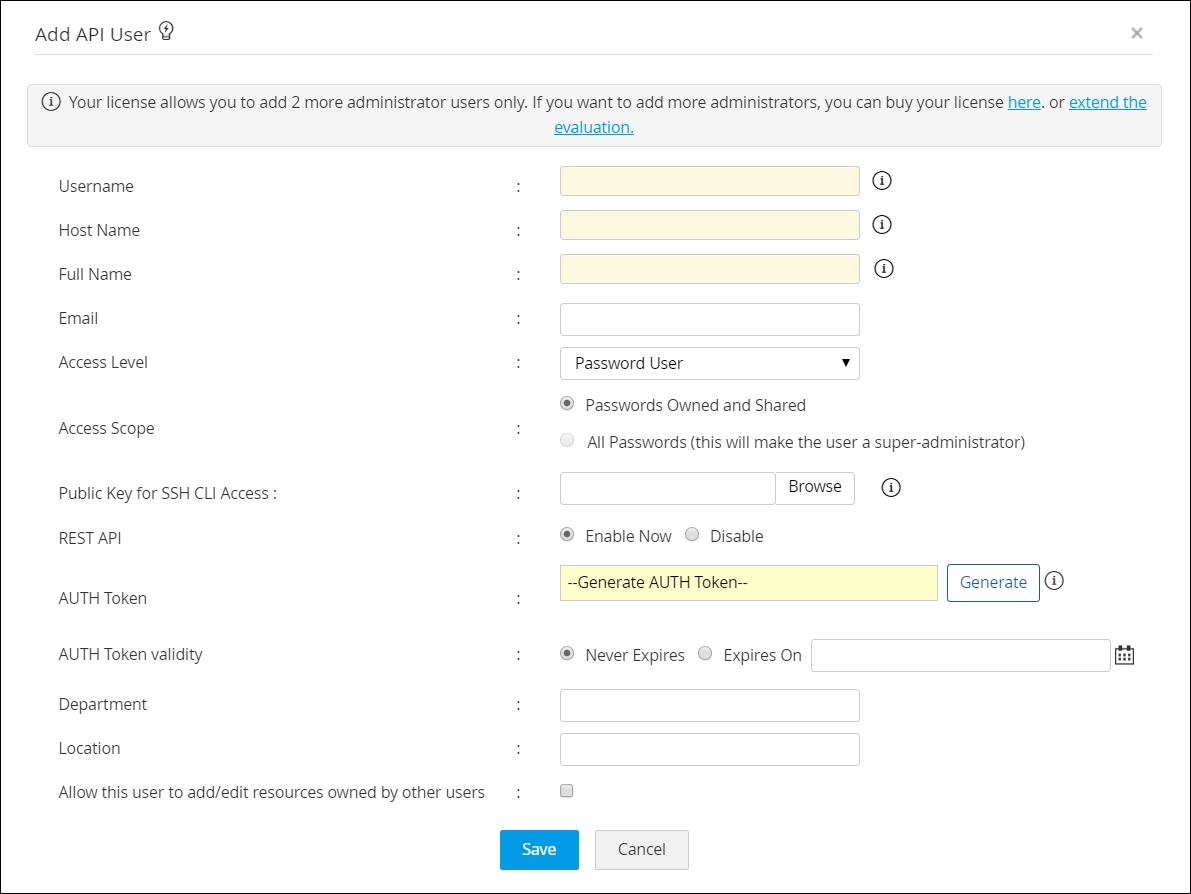
- Once you do this, you will see a text box for the API key. Click on Generate to generate the API key. The API key is the Auth Token for your access purposes. Copy down this key and store it in a secure location for your future reference. This key will be displayed in the GUI only once and if you were to lose it, the key needs to be regenerated from this window.
- You can set a validity period for the API key: by choosing the option Never Expires you can make the key to be valid forever. Otherwise, specify an expiration date.
- Enter the department and location.
- Click Save.
Note: API user creation is specific to the host from where an application contacts PAM360 for passwords. To use Password Management APIs from more than one host, you need to create as many API users as the number of hosts. Conversely, if you wish to have many users on a single host, then again you need to create as many API users as needed.