Importing Users from LDAP
(This procedure is applicable from build 6310)
LDAP (Lightweight Directory Access Protocol) is a widely used standard protocol for accessing and managing directory services that provide a standardized approach to storing and retrieving information about users, devices, and other network resources. In PAM360, you can now integrate your organization's LDAP servers and import users of your organization. Post importation, you can manage their privilege to the respective resources available in the organization.
Similar to importing users from a file, AD, and Microsoft Entra ID, you can also import users from LDAP directory. Read further to know how.
Steps Required for Importing Users
- Configuring LDAP Server in PAM360
- Importing Users from LDAP Server
a. Configuring User Synchronization between LDAP Server and PAM360 - Specifying Appropriate User Roles
- Enabling LDAP Authentication
- Managing LDAP Servers, Organizational Units, and Groups in PAM360
1. Configuring LDAP Server in PAM360
The first step is to provide the required server credential details in PAM360 to configure LDAP Server in PAM360. To do so, navigate to Admin >> Authentication >> LDAP and perform the steps that follow:
- Click the LDAP Server Details button from the LDAP Server Configuration page to add your LDAP server in PAM360. Alternatively, you can also access this page from Users >> Add User >> Import from LDAP.
- In the window that opens, click Add button or Add New Domain icon.
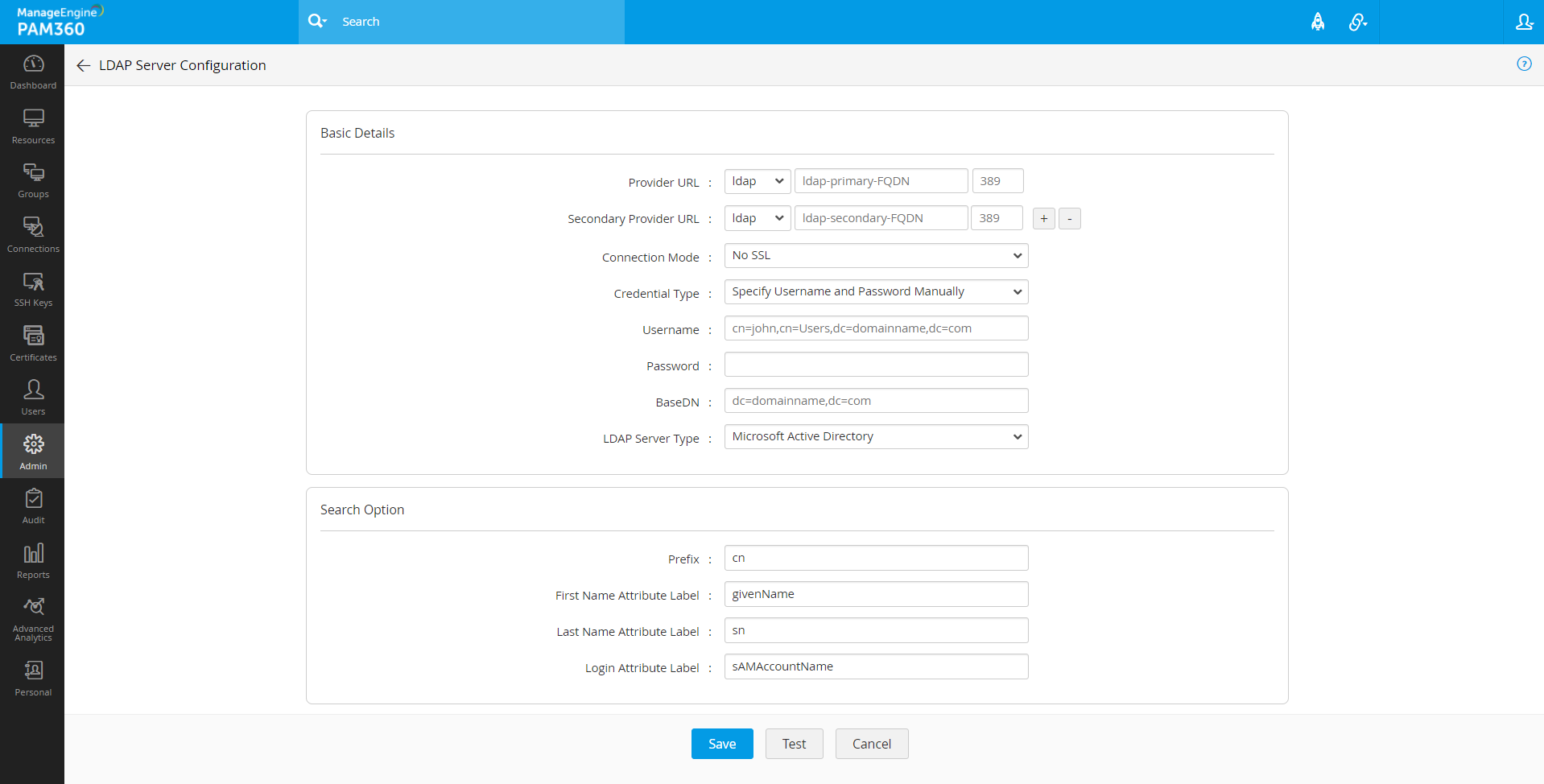
- In the new window that opens, fill in the details as follows:
- Enter the URL of the LDAP provider. For example., ldap pamwinsec23 389.
- You can configure the connection between LDAP Server and PAM360 to be over an encrypted channel (SSL) or Non-SSL. If you choose SSL mode as the connection mode, proceed with the following steps, else proceed with the next subsequent steps.
- To enable the SSL mode, the LDAP server should be serving over SSL in port 636, and you will have to import the LDAP server's root certificate, LDAP server's certificate, and all other certificates that are present in the respective root certificate chain into the PAM360's server machine's certificate store.
- To import certificates, open a command prompt and navigate to <PAM360_SERVER_HOME>\bin directory and execute the following command:
For Windows:
importCert.bat <Absolute Path of certificate>
For Linux:
importCert.sh <Absolute Path of certificate>
- Restart the PAM360 server and continue with the following steps.
- In the supply credentials, select Specify Username and Password manually or Use an account stored in PAM360. If you have selected Use an account stored in PAM360, select the respective LDAP Resource Name and the Account Name from PAM360.
- If you have selected Specify Username and Password manually, enter the credentials of any one of the users already present in LDAP for authentication. It should be in the format of how the user would have submitted their username when authenticating to your application. For example, a typical entry would look something like cn=eric,cn=users,dc=manageengine,dc=com
- Enter the Password of the given user.
- Enter the BaseDN information. This is the 'base' or 'root' from where directory lookups should take place. Enter the LDAP base (top level of the LDAP directory tree). Enter it exactly in the format used in your LDAP. No spaces are allowed between the commas or the '=' equal symbol and entries that are case-sensitive. For example.,dc=manageengine,dc=com.
- Select your LDAP Server Type from the options that follow:
- Microsoft Active Directory
- Novell eDirectory
- OpenLDAP
- Others
- If your LDAP server belongs to the type Microsoft Active Directory/Novell eDirectory/OpenLDAP, click Test.
- Upon successful test validation, click Save.
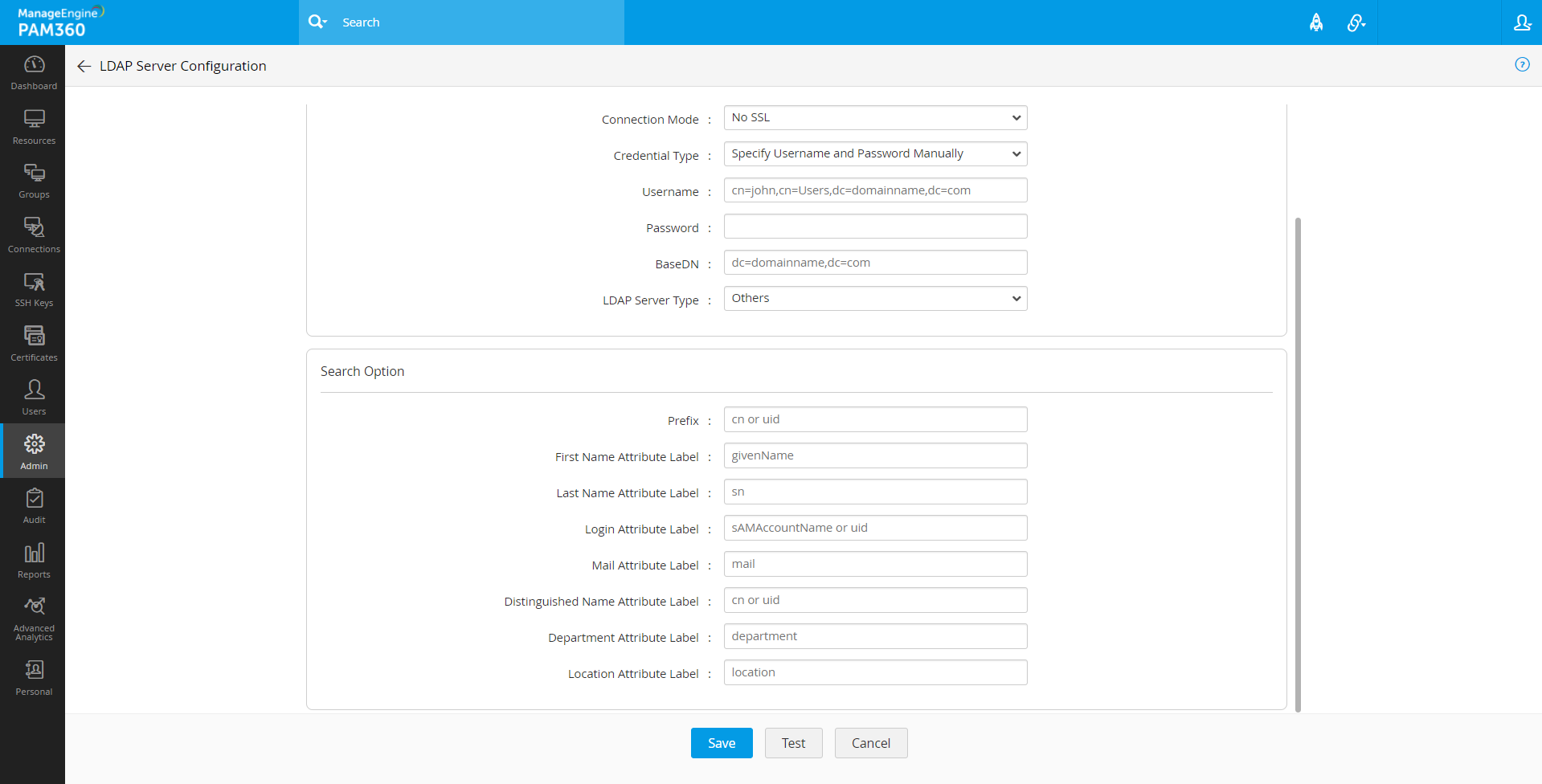
- If your LDAP server belongs to types other than Microsoft Active Directory/Novell eDirectory/OpenLDAP, specify the following additional details to authenticate the users:
- Enter the user login attribute in your LDAP structure in the text field for 'Login Attribute Label'. For instance, for LDAP making use of AD, the entry would be 'sAMAccountName' and for OpenLDAP, the entry would be 'uid'. If you are using any other LDAP, make this entry in accordance with your LDAP structure.
- Enter the e-mail attribute for the users in your LDAP structure in the text field for 'Mail Attribute'. For instance, for LDAP making use of AD, the entry would be 'mail'. If you are using any other LDAP, make this entry in accordance with your LDAP structure.
- Enter the distinguished name attribute - that is the LDAP attribute that uniquely defines this object. For instance, for LDAP making use of AD, the entry would be 'distinguishedName' and for OpenLDAP, the entry would be 'dn'. If you are using any other LDAP, make this entry in accordance with your LDAP structure.
- Enter the remaining attributes accordingly and Save the LDAP server configuration.
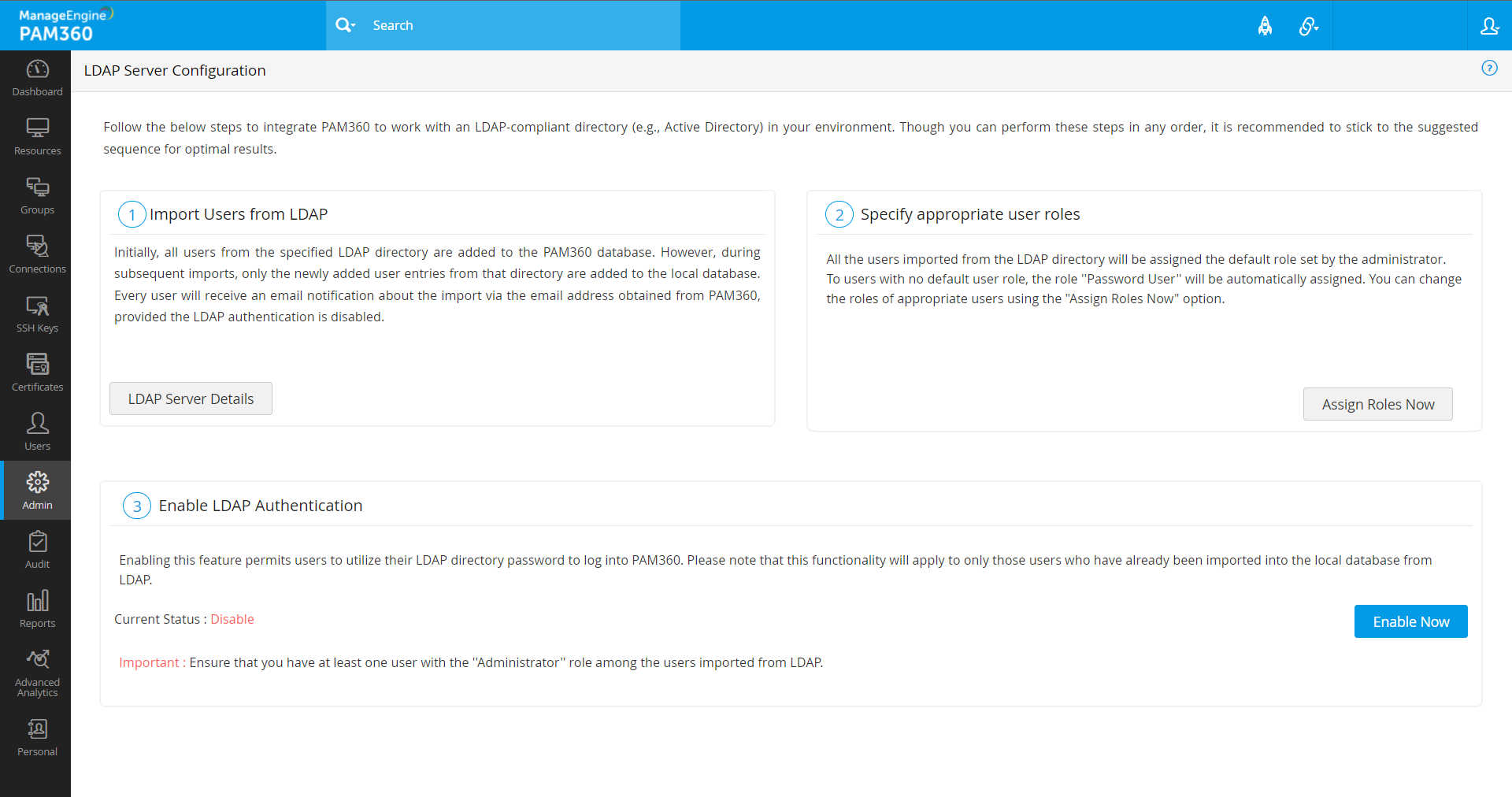
2. Import Users from LDAP
You can import users from LDAP into PAM360 via Organizational Units, Groups, and using Search Filters.
To import users from Groups/Organizational Units:
- Navigate to the LDAP Server Configuration page and click Import >> Groups/Organizational Units.
- In the pop-up that opens, look for the required Groups/Organizational Units using the Search option or the View all Groups/Organizational Units option.
- Select the respective Groups/Organizational Units from the available list and click Save.
- The imported Groups/Organizational Units will be listed in the respective window of the LDAP Server Configuration page.
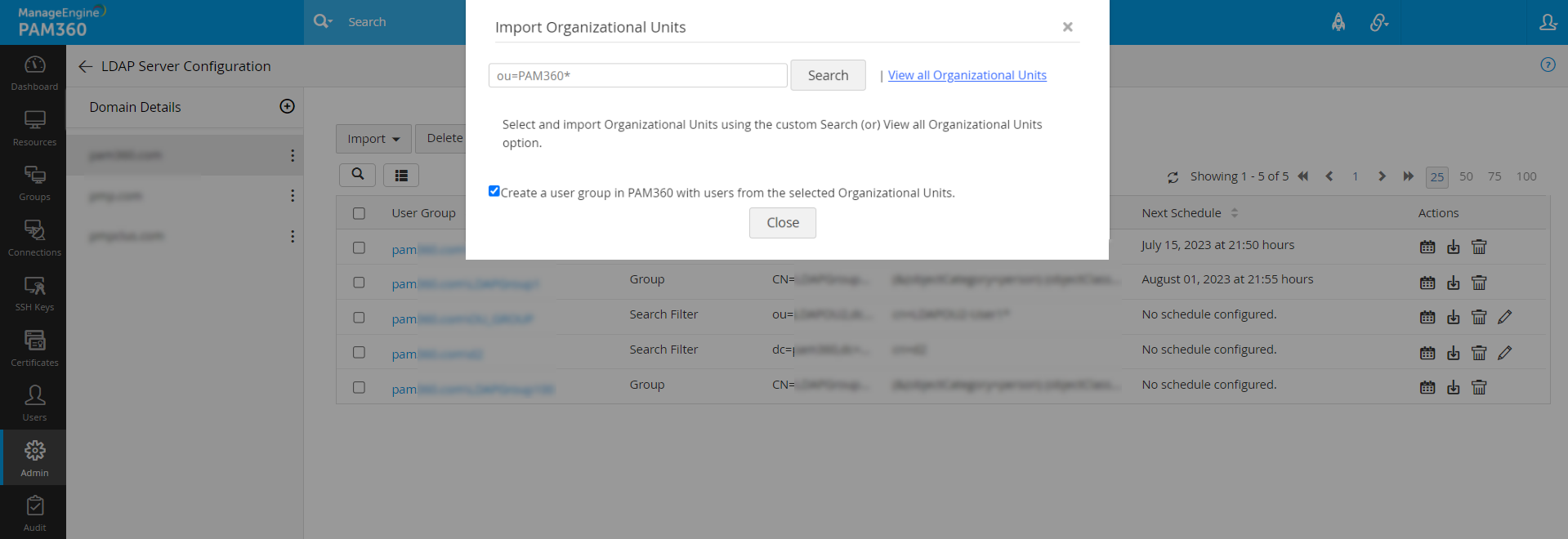
Note: If you need the users present in the selected Group/OU to be created as a specific user group in PAM360, select the 'Create a user group in PAM360 with users from the selected Organizational Units' before you click the Save button.
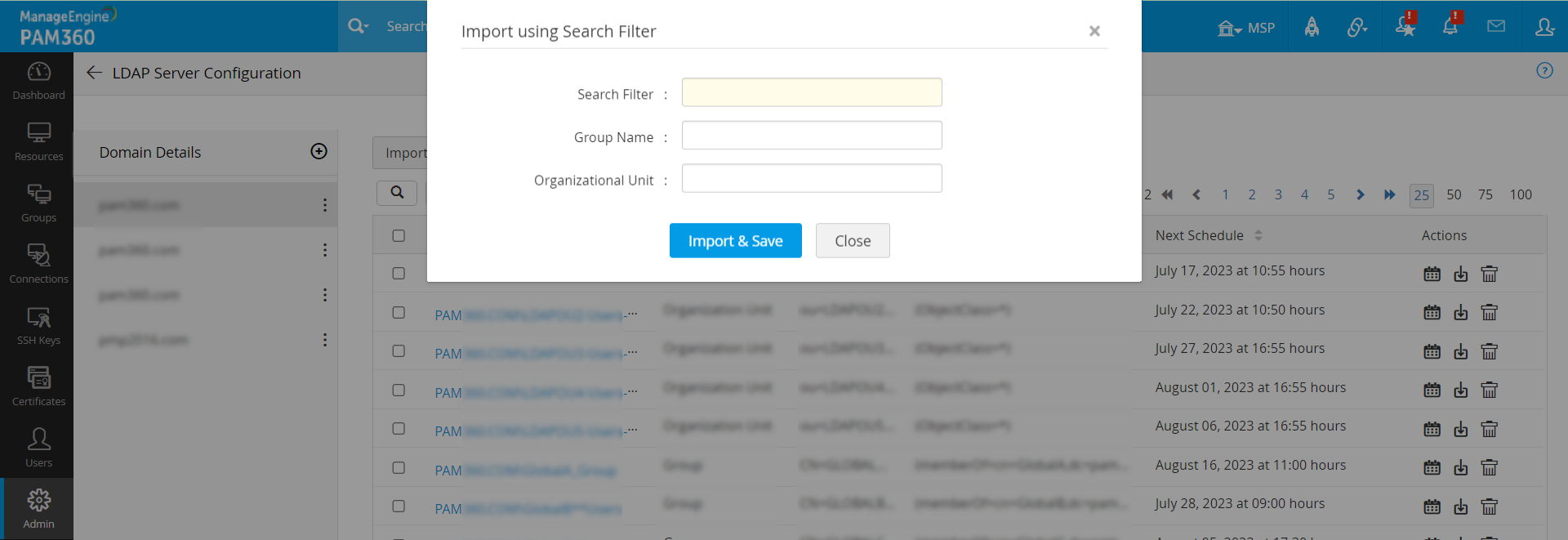
To import the users apart from Groups and Organizational Units, you can utilize the Search Filter option as follows:
- Navigate to the LDAP Server Configuration page and click Import >> Using Search Filter.
- In the pop-up that opens, enter the search filter information and click Save.
- Enter the Group name and the Oragnizational Units as the optional information in which the search filter has to be looked for.
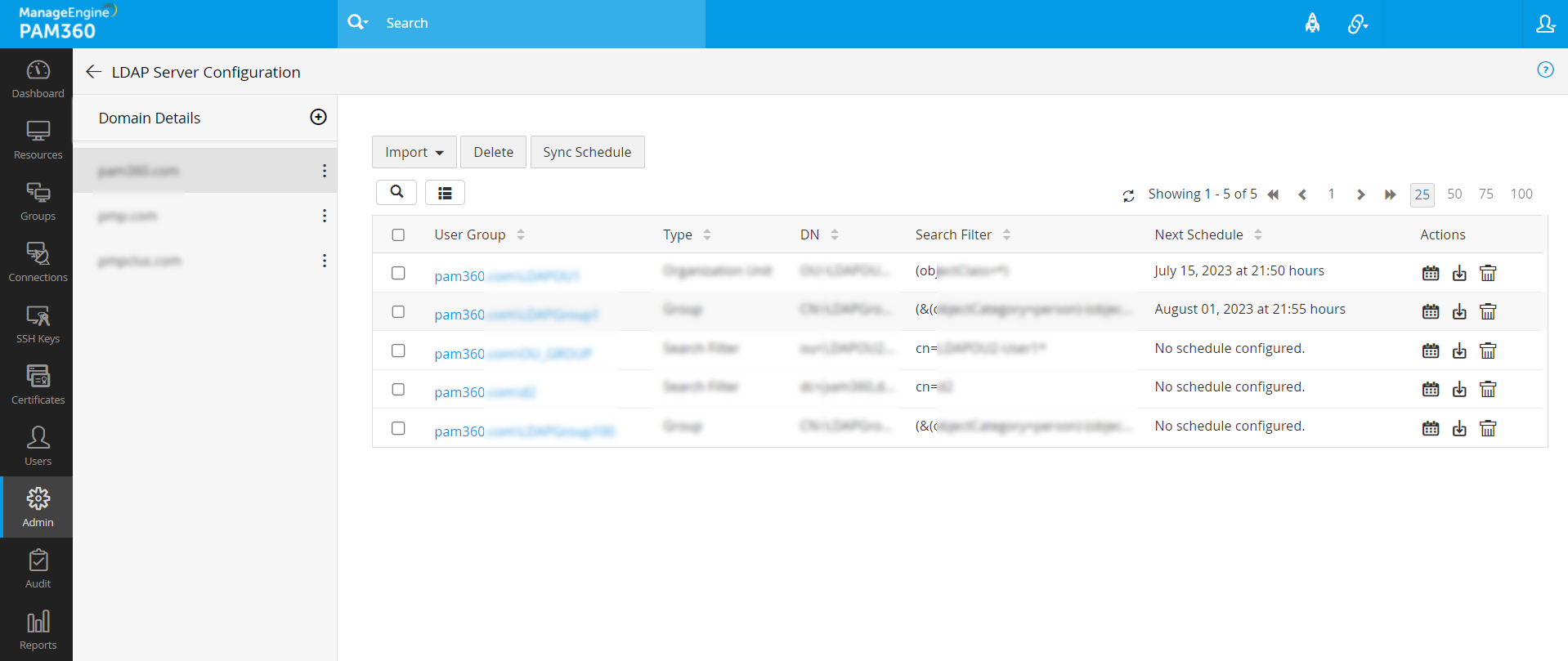
Now, click on the Import from LDAP icon beside the respective Groups/Organizational Units/Search Filter configuration to import the users into PAM360.
Soon after hitting this 'Import from LDAP' button, PAM360 will start adding all users from the respective configurations of the LDAP. During subsequent imports, only the new user entries in LDAP are added to the PAM360. During import, every new user will be notified through email about their account, along with a password that will be used to log in to PAM360 when LDAP authentication is disabled.
2.1 Configure Synchronization between LDAP Server and PAM360
Whenever new users get added to the LDAP, there is a provision to automatically add them to PAM360 and keep the user details in sync. This can be done from the 'LDAP Server Configuration' page in individual or in bulk.
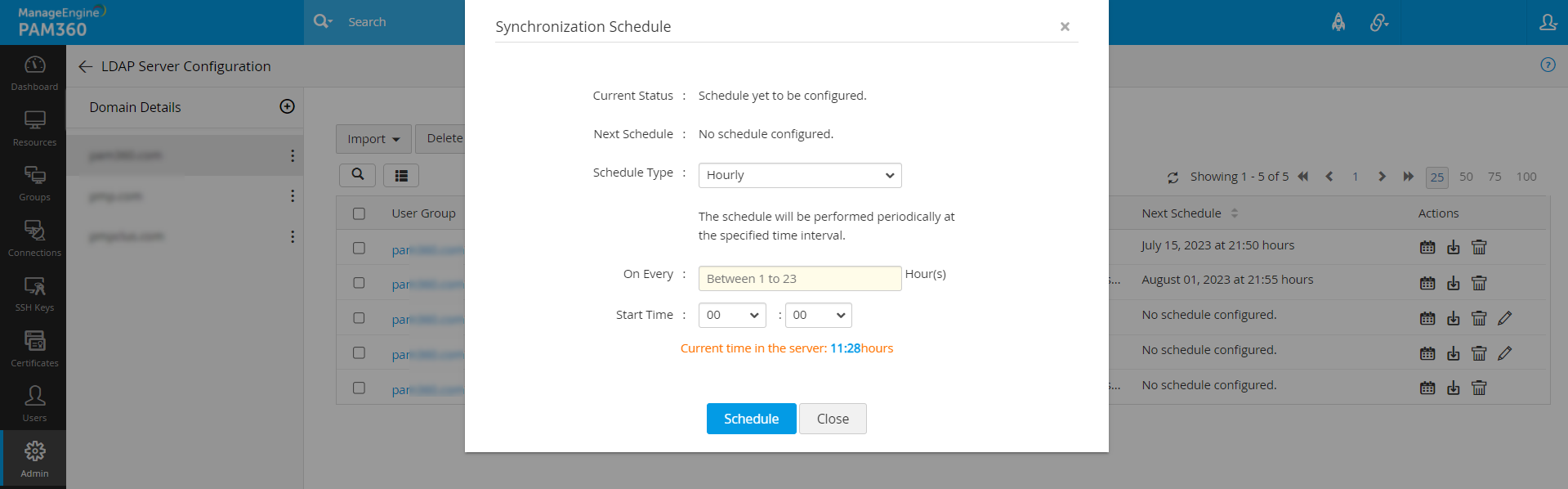
- To synchronize the users from LDAP configuration to PAM360, click on the Sync Schedule icon beside the desired Groups, Organizational Units, or Search Filter.
- In the pop-up that opens, enter the time interval at which PAM360 has to query the LDAP server to keep the user details in sync. The time interval could be as low as a minute, or it can be in the range of hours/days.
- Now, click Save to schedule the synchronization accordingly.
- To schedule the synchronization in bulk,
- Select the desired Organizational Units, Groups, or Search Filters and click the Sync Schedule button at the top pane.
- In the pop-up that opens, enter the time interval at which PAM360 has to query the LDAP server to keep the user details in sync and click Save. The time interval could be as low as a minute, or it can be in the range of hours/days.
3. Specifying Appropriate User Roles
All the users imported from LDAP will be assigned the 'Password User' role by default. To assign specific roles to specific users,
- Navigate to Admin >> Authentication >> LDAP and click Assign Roles Now.
- In the pop-up form that opens, all the users imported from AD will be listed.
4. Enabling LDAP Authentication
The final step is to enable LDAP authentication. After this, your users can use their LDAP directory password to log into PAM360. Please note that this will work only for users who were already imported to the PAM360 from LDAP.
Note: Make sure you have at least one user with the 'Administrator' role among the users imported from LDAP.
5. Managing LDAP Servers, Organizational Units, and Groups in PAM360
Navigate to Admin >> Authentication >> LDAP >> LDAP Server Details. In the window that opens,
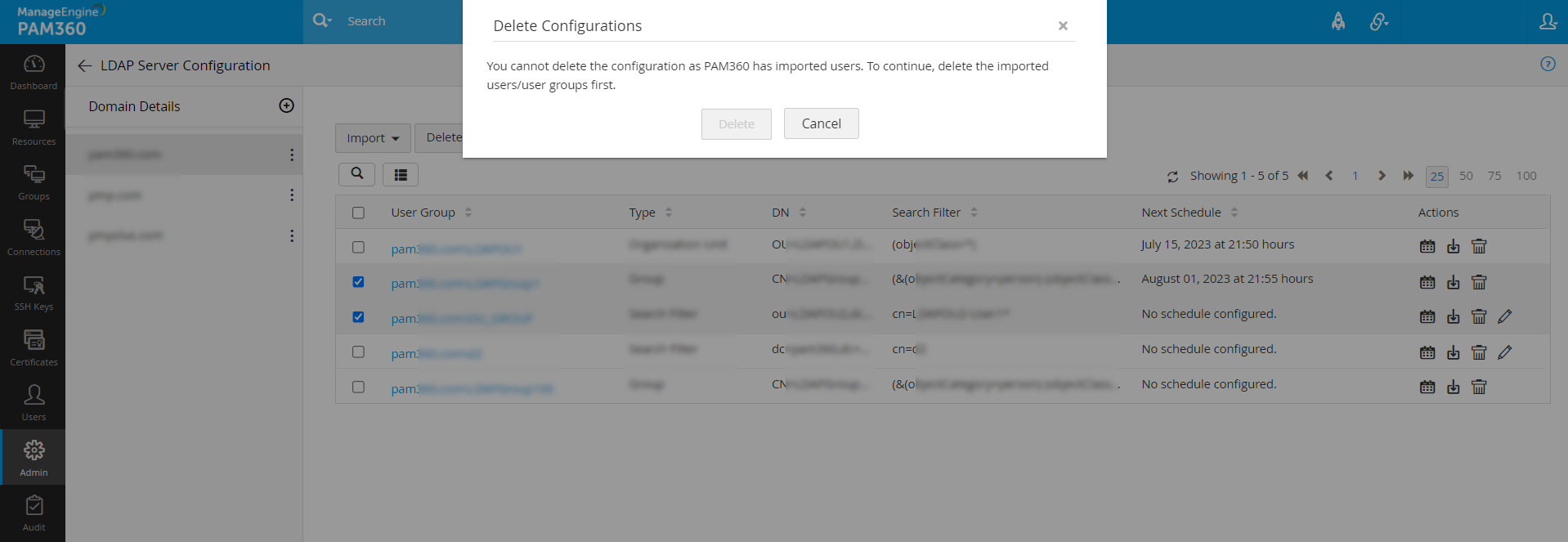
- Click the kebab menu icon () beside the respective LDAP server to delete the existing one or edit entries pertaining to the LDAP server.
- Click the delete icon beside the respective OU, Group, or Search Filter to delete the imported LDAP configurations from PAM360. In addition, you can also perform this operation in bulk by selecting the respective Organizational Units, Groups, or Search Filter and clicking on the Delete button at the top pane.
Note: The deletion of Groups, Organizational Units, and Search Filters will exclusively remove their respective entries from the PAM360 database and will not impact any data within the LDAP server.