If you love to keep up with the buzz and latest trends in cybersecurity, then you must have come across the term cybersecurity mesh. Gartner, a leading IT research and consulting firm, predicts that by 2024, the organizations adopting a cybersecurity mesh architecture will be able to reduce the financial impact of security incidents by an average of 90%.
The above statistic is indeed a promising and optimistic one! But, it brings us to an obvious question: What is cybersecurity mesh?
In this blog, we'll discuss cybersecurity mesh, its different layers, and its advantages to the cyber industry.
Gartner describes cybersecurity mesh as "a flexible, composable architecture that integrates widely distributed and disparate security services."
It is a security approach that allows organizations to transition from an isolated model of security to a better and more flexible security model. This is achieved through a set of supportive layers, which allows different security solutions and tools to interoperate and provide cohesive and holistic defenses for the organization.
It provides a framework for the various security tools deployed in isolation from each other to work collaboratively to achieve a common goal of defending organizations and meeting their expanding security requirements.
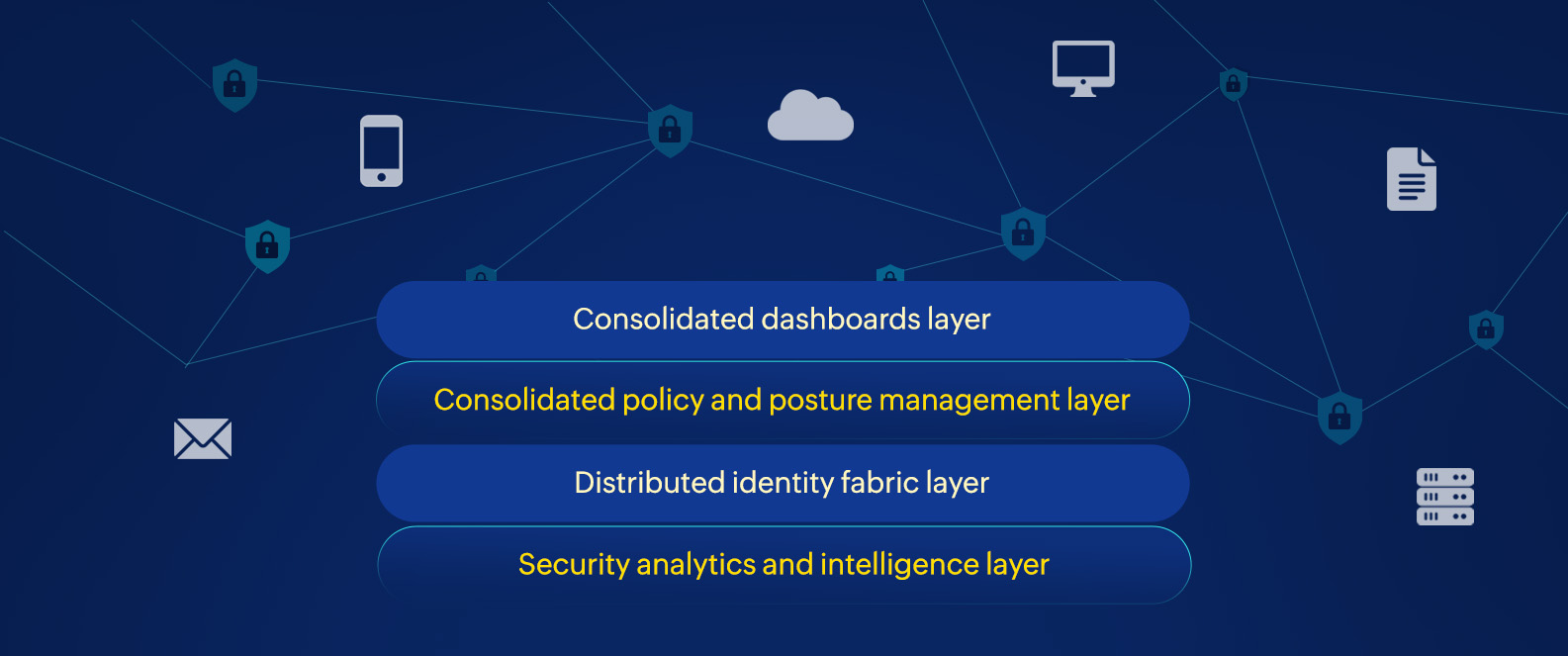
Organizations can build their cybersecurity mesh architectures (CSMAs) on Gartner's four foundational layers. These layers are:
Security solutions at this layer are required to collect, assemble, and analyze enormous amount of data from multiple security tools. This layer also focuses on collecting and analyzing data from past cyberthreats to improve future defense response actions.
Security solutions at this layer facilitate capabilities like identity and access management services, directory services, decentralized identity management, entitlement management, and identity proofing.
Security solutions at this layer translate the policies of individual security tools into the foundational rules and configuration settings. This helps in achieving an effective posture across different environments by consolidating the individual policies as a whole.
The CSMA at this layer aims to offer a holistic and composite view of the security infrastructure to provide better detection and faster responses to threats. It equips security teams with granular visibility on the security ecosystem.
With the ever-evolving threat landscape, cyberattacks have become more sophisticated; more than ever before, organizations need to redefine their defense strategies by adopting new security frameworks and approaches. Here are few of the advantages of CSMA:
Adopting the cybersecurity mesh approach is one of the viable and efficient ways in which organizations can protect their security infrastructure and create an environment that is not only secure, but scalable.
Hope this blog helped you in understanding why the CSMA is trending in the cyber world. Stay tuned for more blogs on trending topics!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.